- January 22, 2016
- Posted by: isoqaruser
- Categories:


Within the 12 core requirements of the PCI DSS, there are five new sub-requirements for service providers affecting requirements 3, 10, 11 and 12. New sub-requirements have been added to requirement 8 to ensure multi-factor authentication is used for all non-console administrative access and all remote access in the cardholder data environment. There are also two new appendices. Appendix A2 incorporates new migration deadlines for removal of Secure Sockets Layer (SSL) /early Transport Layer Security (TLS) in line with the December 2015 bulletin. Appendix A3 incorporates the “Designated Entities Supplemental Validation” (DESV), which was previously a separate document.
HOW LONG DO ORGANIZATIONS HAVE TO IMPLEMENT PCI DSS 3.2?
PCI DSS 3.1 has retired on 31 October 2016, and after this time all assessments will need to use version 3.2. Between now and 31 October 2016, either PCI DSS 3.1 or 3.2 may be used for PCI DSS assessments. The new requirements introduced in PCI DSS 3.2 are considered best practices until 31 January 2018. Starting 1 February 2018 they are effective as requirements and must be used.
PCI DSS 3.2 marks the start of refining the payment data regulations, rather than minor changes, and includes requirements to strengthen encryption and multifactor authentication.
The PCI Security Standards Council (PCI SSC) has published a new version of its data security standard (DSS), used to safeguard payment data before, during and after a purchase is made. PCI DSS version 3.2 replaces version 3.1, which has expired on Oct. 31.
Multifactor Authentication ¬ – One significant change in PCI DSS 3.2 is that it includes multi-factor authentication as a requirement for any personnel with administrative access into environments handling card data. Previously this requirement applied only to remote access from untrusted networks.
“A password alone should not be enough to verify the administrator’s identity and grant access to sensitive information,” said PCI Security Standards Council CTO Troy Leach. “We’ve seen an increase in attacks that circumvent a single point of failure, allowing criminals to access systems undetected and to compromise card data.”
Platinum Principles for continual PCI
1. KNOW THE STANDARD
Unlike many other compliance standards e.g. ISO 27001 (too generic) and SSAE 16 (you can define your own frequency), PCI DSS has a definite frequency for maintaining controls. There are multiple requirements which could have a cascading effect on your compliance posture if you fail to maintain the effectiveness of the required controls.
There could be various teams involved and unless there is a crystal clear understanding and communication within the teams, you are most likely to face difficulties. For example – the purchase is done by procurement team, device hardening is done by some other team and vulnerability scanning is someone else’s responsibility. Unless these teams are in sync and know the standard well, maintenance becomes difficult.
2. GET THE NECESSARY BUDGETARY APPROVAL FOR THE UPKEEP
As a CISO, you may need to procure stuff and outsource some of your activities viz. Scans from ASV and other periodic scans. While submitting the budget, it is advisable to include the recurring maintenance cost as well. This will ensure that you have necessary funds available and you don’t need to run at the eleventh hour and delay the mandatory requirements for compliance.
3. DEVELOP AN ANNUAL COMPLIANCE CALENDAR
A simple spreadsheet can do wonders. List the tasks as Daily (Log Reviews), Weekly (File Integrity Checks), Monthly (Newly Added Devices, Employee Background Checks, Recent Infrastructure Changes etc.), Quarterly (Scans), Semi-Annually (Network device rule set reviews) and annually (policy reviews, risk assessment, training programs, pen tests, incidents).Once the list is ready, name the “Owner” for each activity. Add the column “Checker”. Circulate the calendar to all the relevant stakeholders.
4. ASSIGN TASKS AND MONITOR THEM
Once the calendar is circulated, ask all the checkers to report the progress on a periodic basis. My strong recommendation – do this on a fortnight basis. This will ensure in initiating the immediate corrections and corrective actions if something is amiss and will not come as a last minute surprise or show spoiler. Our sincere advice – For any challenges, take required advice from the QSA Company. They will guide in addressing any bottlenecks. Remember – hiding facts helps nobody in compliance
5. INCLUDE VENDORS IN COMPLIANCE PROGRAM
Communicate your compliance requirements to the vendors well in advance; in fact, it needs to be a contractual obligation. Vendors play a vital role in maintaining the compliance program when it comes to PCI DSS. If you have third party vendors, keep them well informed. If you have outsourced any of your activities, get the records well in time to avoid last minute hiccups. You’re also now required to maintain a formal list of PCI responsibilities shared with vendors, down to the specific requirements you and the vendor handle. Vendor non-compliance can become a big challenge for your own maintenance and could be a show stopper.
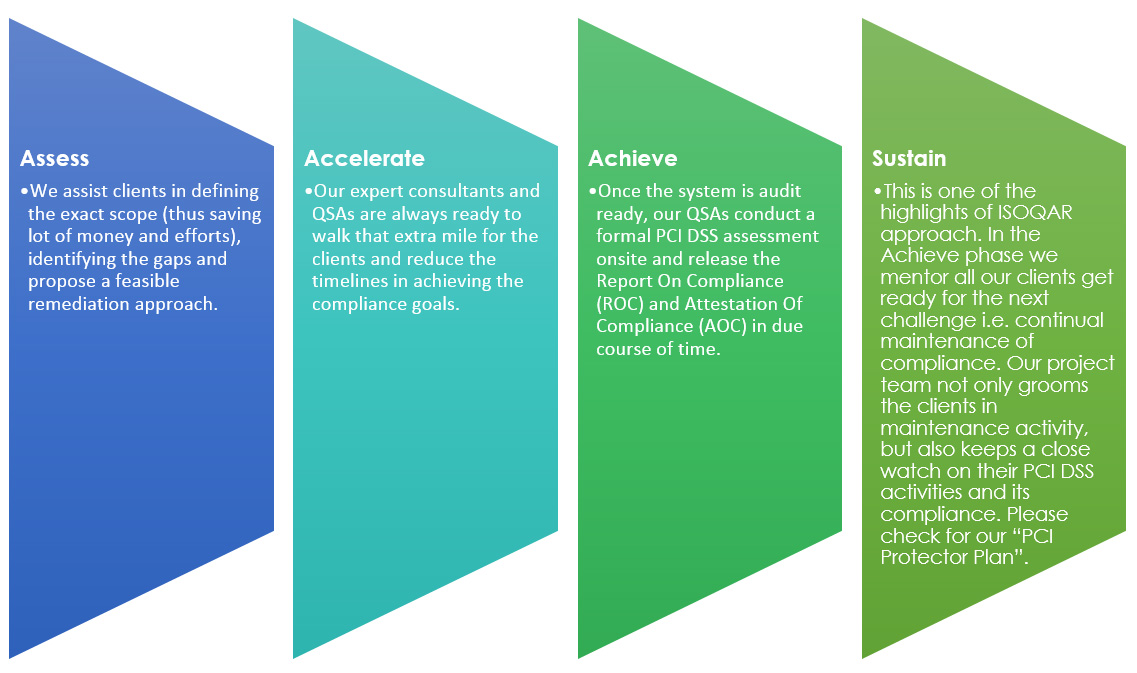
ISOQAR PCI DSS VALUE PROPOSITION BY FOUR FOLD (TRIPLE A -S) APPROACH
We at Alcumus ISOQAR India realize the pains in achieving any compliance and maintaining it.
Specifically, when it comes to achieving and maintaining the PCI DSS compliance the mission is even tougher.
CONCLUSION:
It’s very correctly said “SURVIVAL OF THE FITTEST”. To survive organization needs both proactive and reactive strategy and systems. In today’s scenario, disruption is unacceptable to any customer/ end user. We all need seamless services. Minimize the business impact by adopting a robust business continuity management system.
Risk management – Before an incident and BCMS – after an incident. These are two components business needs today to survive in the competitive world.
